Are you curious about “Stealers Game” and how to stay safe from information-stealing malware targeting Polar product users? This article from polarservicecenter.net dives into the details of these malicious campaigns and provides actionable steps to protect your digital life and Polar devices. We’ll equip you with the knowledge to recognize and avoid these threats. Stay vigilant, update your security measures, and let’s keep your Polar experience secure with product support, data protection and software updates.
1. What Exactly Is a Stealers Game?
A “stealers game” is a deceptive tactic where cybercriminals lure victims into downloading and installing malware disguised as a legitimate video game. The goal is to steal sensitive information, like passwords, financial data, and even cryptocurrency wallet details. These “games” are actually information-stealing Trojans, such as Nova Stealer, Ageo Stealer, or Hexon Stealer, designed to compromise your system and data.
Stealers games often spread through direct messages on platforms like Discord, text messages, or emails, promising beta access to a new video game. These messages often appear to come directly from the game developer to build trust. If a victim shows interest, they receive a download link and password for an archive containing the “installer.” These archives are often hosted on compromised accounts on legitimate platforms like Dropbox, Catbox, or Discord’s Content Delivery Network (CDN), further increasing the illusion of legitimacy.
2. How Do Stealers Games Spread Malware?
The primary method involves tricking users into downloading and executing malicious files disguised as game installers. The files are often packaged as archives (like ZIP or RAR) to bypass initial security checks. Once the user extracts and runs the “installer,” the malware is silently installed in the background.
The Nova Stealer and Ageo Stealer operate on a Malware-as-a-Service (MaaS) model. This means that the developers rent out the malware and its infrastructure to other criminals, expanding its reach and impact. These stealers target credentials stored in browsers, session cookies for platforms like Discord and Steam, and information related to cryptocurrency wallets. A Discord webhook is often used to alert the criminals when new data is stolen, allowing them to react quickly.
Hexon stealer, a relatively new threat, is based on Stealit Stealer code and focuses on stealing Discord tokens, 2FA backup codes, browser cookies, autofill data, saved passwords, credit card details, and cryptocurrency wallet information.
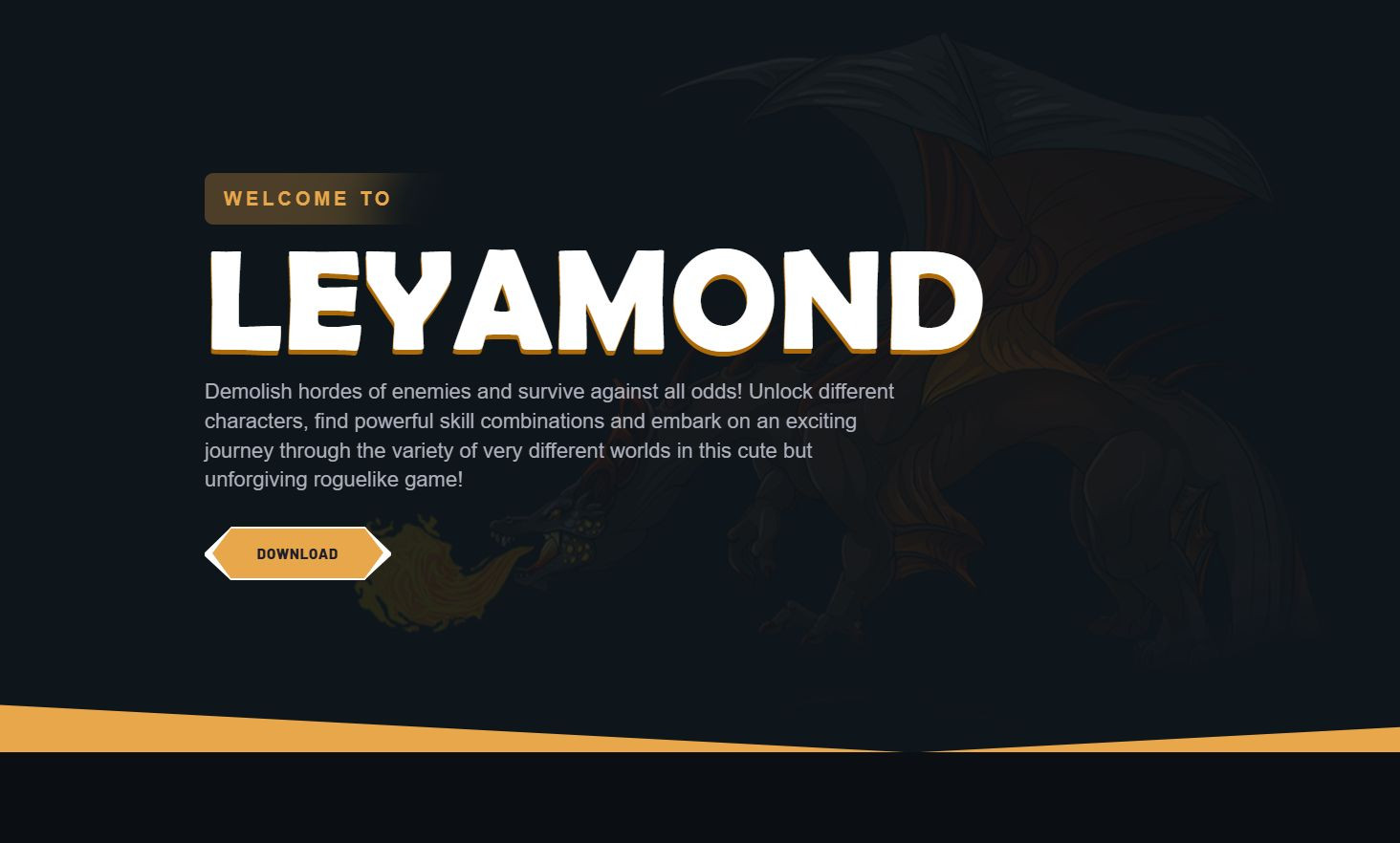 Example of the templated fake website
Example of the templated fake website
3. What Are the Main Targets of Information Stealers?
The primary target is Discord credentials, which criminals use to expand their network of compromised accounts. By gaining access to Discord accounts, they can impersonate the victim and trick their friends and contacts into falling for scams and malware campaigns.
The end goal of these scams, like most others, is monetary gain. Financial information, cryptocurrency wallets, and personal data are all valuable assets for cybercriminals.
4. What Are the Risks of Falling for a Stealers Game?
Falling victim to a stealers game can have severe consequences, including:
- Identity Theft: Stolen personal information can be used to open fraudulent accounts, apply for loans, and commit other forms of identity theft.
- Financial Loss: Stolen financial data, such as credit card details and banking information, can lead to significant financial losses.
- Compromised Accounts: Stolen credentials can be used to access your online accounts, including email, social media, and financial accounts.
- Malware Infection: The malware installed by stealers games can further infect your system with other malicious software, such as ransomware or keyloggers.
- Reputation Damage: If your accounts are used to spread malware or scams, it can damage your reputation and relationships.
5. How Can I Recognize Fake Game Websites?
One common tactic is to use standardized website templates. This allows criminals to quickly change the name and location of the “game” while maintaining a consistent look and feel.
These websites are often hosted by companies that are slow to respond to takedown requests and are protected by Cloudflare, which makes it difficult to identify and shut down the sites.
Another tactic is to use blogspot to host the malware. These sites have a different, but also standard, design.
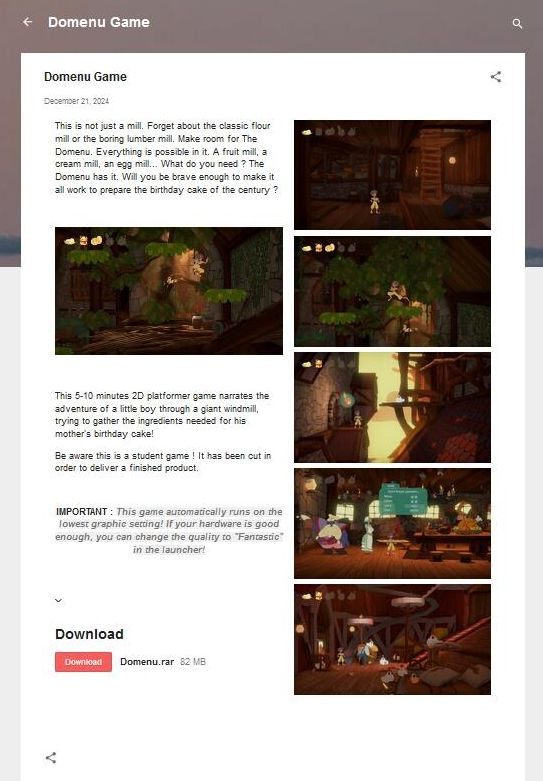 fake game site on blogspot
fake game site on blogspot
6. What Are Some Effective Measures to Stay Safe?
Protecting yourself from stealers games and other malware threats requires a multi-layered approach:
- Use an Anti-Malware Solution: Ensure you have an up-to-date and active anti-malware solution on your computer.
- Verify Invitations: Always verify invitations from “friends” through a different channel, such as texting them directly or contacting them on another social media platform. Remember, their current account may have been compromised.
- Be Wary of Unsolicited Messages: Avoid acting upon unsolicited messages and emails, especially when they ask you to download and install something.
- Practice Safe Browsing: Be cautious about clicking on links or downloading files from unknown sources.
- Keep Software Updated: Keep your operating system, web browser, and other software updated with the latest security patches.
- Use Strong Passwords: Use strong, unique passwords for all your online accounts.
- Enable Two-Factor Authentication: Enable two-factor authentication (2FA) whenever possible to add an extra layer of security to your accounts.
7. How Can Polar Product Users Stay Safe From Targeted Attacks?
Polar product users should be particularly vigilant about protecting their devices and data. Here are some specific steps you can take:
- Download Software Only From Official Sources: Only download Polar software and updates from the official Polar website or authorized app stores.
- Be Wary of Phishing Emails: Be cautious of emails that appear to be from Polar asking for your personal information or login credentials. Always verify the sender’s address and avoid clicking on links in suspicious emails.
- Protect Your Polar Account: Use a strong, unique password for your Polar account and enable two-factor authentication if available.
- Keep Your Polar Device Updated: Regularly update the firmware on your Polar device to ensure you have the latest security patches.
- Monitor Your Polar Data: Regularly monitor your Polar data for any suspicious activity or unauthorized access.
For additional tips and support, visit polarservicecenter.net to learn more about protecting your Polar products.
8. What Are the Latest Developments in Stealer Malware?
Staying informed about the latest developments in stealer malware is crucial for staying ahead of the threats. Some recent trends include:
- Increased Use of MaaS: The rise of Malware-as-a-Service (MaaS) has made it easier for criminals to access and deploy stealer malware.
- Targeting of Cryptocurrency: Cryptocurrency wallets and exchanges are increasingly being targeted by stealer malware.
- Sophisticated Social Engineering: Cybercriminals are using more sophisticated social engineering tactics to trick victims into downloading and installing malware.
- Evasion Techniques: Stealer malware is becoming more sophisticated in its ability to evade detection by anti-malware software.
9. How Does polarservicecenter.net Help Protect Polar Users?
polarservicecenter.net is dedicated to providing Polar users with the resources and support they need to stay safe online. We offer:
- Up-to-Date Information: We provide the latest information about stealer malware and other threats targeting Polar users.
- Security Tips: We offer practical tips and advice on how to protect your Polar devices and data.
- Troubleshooting Guides: We provide detailed troubleshooting guides to help you resolve any security issues you may encounter.
- Authorized Service Centers: We can connect you with authorized Polar service centers for professional assistance with your devices.
- Warranty Information: We provide clear and concise information about Polar warranties and coverage.
By visiting polarservicecenter.net, you can access a wealth of resources to help you stay safe and get the most out of your Polar products.
10. What Should I Do If I Think I’ve Been Hacked?
If you suspect that you’ve fallen victim to a stealers game or other malware attack, take the following steps immediately:
- Disconnect From the Internet: Disconnect your computer from the internet to prevent further data theft.
- Run a Full System Scan: Run a full system scan with your anti-malware software to detect and remove any malware.
- Change Your Passwords: Change your passwords for all your online accounts, including email, social media, and financial accounts.
- Enable Two-Factor Authentication: Enable two-factor authentication (2FA) on all your accounts that support it.
- Monitor Your Accounts: Monitor your accounts for any suspicious activity, such as unauthorized transactions or login attempts.
- Report the Incident: Report the incident to the relevant authorities, such as the Federal Trade Commission (FTC) or your local law enforcement agency.
- Contact Polar Support: Contact Polar support for assistance with securing your Polar device and data.
IOCs (Indicators of Compromise)
Here are some Indicators of Compromise (IOCs) associated with stealers games:
Download Sites:
- dualcorps[.]fr
- leyamor[.]com
- crystalsiege[.]com
- crystalsiege[.]online
- dungeonofdestiny[.]pages.dev
- mazenugame[.]blogspot.com
- mazenugames.[]blogspot.com
- yemozagame[.]blogspot.com
- domenubeta[.]blogspot.com
- domenugame[.]blogspot.com
Protect Your Social Media
Cybersecurity risks should never spread beyond a headline. Protect your social media accounts by using Malwarebytes Identity Theft Protection.
Protecting Your Polar Device and Data
- Strong Passwords: Utilize robust and unique passwords for your Polar account and all associated services. A password manager can assist in generating and securely storing these.
- Two-Factor Authentication (2FA): Enable 2FA wherever possible. This adds an extra layer of security, requiring a verification code from your phone or another device in addition to your password.
- Software Updates: Keep your Polar device’s firmware and any related apps on your smartphone or computer updated to the latest versions. These updates often include security patches that address newly discovered vulnerabilities.
- Beware of Phishing: Be cautious of emails, messages, or calls that ask for your Polar account information or direct you to suspicious websites. Always verify the sender’s authenticity before providing any sensitive data. Phishing attempts can be quite convincing.
- Secure Wi-Fi: When syncing your Polar device, use a secure, private Wi-Fi network. Avoid public Wi-Fi networks, as they are often less secure and may be vulnerable to eavesdropping.
- Data Encryption: Explore options for encrypting the data on your Polar device, if available. This protects your personal information even if the device falls into the wrong hands.
- Regular Backups: Back up your Polar data regularly to a secure location. This ensures you can recover your information in case of device loss or compromise.
- Review Connected Apps: Periodically review the apps connected to your Polar account and revoke access to any apps you no longer use or trust.
- Monitor Account Activity: Keep an eye on your Polar account activity for any unusual or unauthorized access. Report any suspicious activity to Polar support immediately.
- Factory Reset: If you sell or give away your Polar device, perform a factory reset to wipe all your personal data from the device.
FAQ: Stealers Game
1. What makes stealers game attacks so dangerous?
Stealers game attacks are dangerous because they combine social engineering with malware. They trick you into thinking you’re downloading a legitimate game, when in reality you’re installing malware that steals your personal information.
2. How can I tell if a game download is fake?
Be suspicious of unsolicited messages offering beta access, especially if they come with a download link and password. Verify the source independently and check for red flags like poor grammar, typos, or an unusual website address.
3. What types of information do stealers games target?
Stealers games target a wide range of information, including usernames, passwords, financial data, credit card details, cryptocurrency wallet information, and personal data.
4. Can stealers games affect my Polar device directly?
While stealers games primarily target computers and smartphones, they can indirectly affect your Polar device if you use the same credentials on your Polar account. If your Polar account is compromised, criminals could access your fitness data and other personal information.
5. What should I do if I accidentally downloaded a stealers game?
Disconnect your computer from the internet immediately. Run a full system scan with your anti-malware software. Change your passwords for all your online accounts, including email, social media, and financial accounts.
6. Are there specific anti-malware programs that are better at detecting stealers games?
Most reputable anti-malware programs should be able to detect stealers games. Make sure your anti-malware software is up-to-date and has real-time protection enabled. Malwarebytes is a well-regarded option.
7. How often should I change my passwords to protect against stealers games?
It’s a good practice to change your passwords every three to six months, or immediately if you suspect your account has been compromised.
8. What is two-factor authentication, and how does it help?
Two-factor authentication (2FA) adds an extra layer of security to your accounts by requiring a verification code from your phone or another device in addition to your password. This makes it much harder for criminals to access your accounts, even if they have your password.
9. What resources does polarservicecenter.net provide for Polar users concerned about security?
polarservicecenter.net provides up-to-date information about security threats, practical tips for protecting your devices and data, troubleshooting guides, and contact information for authorized service centers. We are your dedicated resource for all things Polar.
10. Where can I report a suspected stealers game or phishing attempt targeting Polar users?
You can report suspected stealers games or phishing attempts to the Federal Trade Commission (FTC) and to Polar support.
Navigating the digital world requires constant vigilance, especially when dealing with potential threats like stealers games. Remember to stay informed, be cautious about unsolicited messages and downloads, and utilize the resources available at polarservicecenter.net to safeguard your Polar devices and personal information. Staying ahead of these threats is essential for a secure and enjoyable experience with your Polar products.
Address: 2902 Bluff St, Boulder, CO 80301, United States.
Phone: +1 (303) 492-7080.
Website: polarservicecenter.net.
By implementing these strategies and staying informed, you can significantly reduce your risk of falling victim to stealers games and other malware threats. Remember, a proactive approach to security is the best defense.