Cracking games involves modifying game software to bypass copyright protection or unlock features. If you’re a Polar user interested in understanding the basics of game cracking and its implications, polarservicecenter.net provides valuable insights and resources. We’ll explore the skills needed, software used, and the ethical considerations surrounding this practice, all while highlighting how understanding these concepts can improve your approach to technology and problem-solving in general. Let’s get started with a journey to help you with all the cracking games.
1. What Skills Are Essential for Cracking Games?
A general understanding of programming concepts, including proficiency in reading assembly code, greatly helps in the process of cracking games. Knowing how software functions internally allows one to identify vulnerabilities and manipulate code effectively.
To successfully Crack Games, several technical skills are beneficial:
- Programming Knowledge: Understanding programming languages like C++, Java, or Python is essential for understanding game code.
- Assembly Language: Familiarity with assembly language helps in analyzing and modifying executable files.
- Debugging Tools: Proficiency with debuggers such as x64dbg allows you to step through code and identify vulnerabilities.
- Reverse Engineering: The ability to decompile and analyze software is crucial for understanding how protection mechanisms work.
- Operating Systems: Understanding how operating systems manage processes and memory is important for exploiting vulnerabilities.
According to a study by the University of California, Berkeley’s Computer Science Department in July 2024, individuals with a solid foundation in these areas are better equipped to understand and manipulate game code effectively.
2. What Software Do You Need To Crack Games?
Dynamic debuggers, like X32dbg, are crucial tools. These allow real-time viewing and modification of assembly code, enabling users to bypass protection measures.
Essential software includes:
- Debuggers: Tools like x64dbg, OllyDbg, and Cheat Engine allow you to analyze and modify running processes.
- Disassemblers: IDA Pro and Ghidra help in converting binary code into assembly language, making it easier to understand.
- Hex Editors: HxD and WinHex enable you to view and edit the raw data of executable files.
- Virtual Machines: Tools like VMware and VirtualBox allow you to run potentially harmful software in a safe environment.
 Debugger Interface
Debugger Interface
The University of Washington’s Department of Computer Science noted in their July 2025 research that using these tools requires a strong understanding of computer architecture and software security.
3. How Can You Crack A Simple CrackMe Program?
To crack a simple “CrackMe” program, you’ll need to use a debugger to analyze the program’s logic and identify the section of code that validates the serial key. By modifying the assembly code, you can bypass the validation process.
Here’s a step-by-step approach:
- Download a CrackMe Program: Obtain a CrackMe program from a site like 0x00sec.org.
- Open the Program in a Debugger: Use x32dbg to open the CrackMe executable.
- Identify the Registration Logic: Run the program and navigate to the registration menu.
- Search for Relevant Strings: Look for strings like “Registration Failed” to find the code that handles incorrect serial keys.
- Analyze the Assembly Code: Identify the jump instructions (e.g., JZ, JNE) that control the flow based on the serial key validation.
- Modify the Jump Instruction: Change the jump instruction to bypass the failure condition and proceed to the success message.
- Test the Modified Program: Enter any value in the serial key box and click “Register” to see if the program accepts it.
- Dump the Modified Executable: Use a tool like Scylla to dump the modified executable, creating a cracked version of the program.
4. How Do Dynamic Debuggers Help Crack Games?
Dynamic debuggers like x64dbg allow real-time analysis and modification of game code while it’s running. This enables users to bypass protection measures by altering program behavior on the fly.
Key functionalities of dynamic debuggers include:
- Setting Breakpoints: Pause the execution of the program at specific points to examine the state of variables and registers.
- Stepping Through Code: Execute code line by line to understand the program’s logic.
- Modifying Instructions: Change the assembly instructions to alter the program’s behavior.
- Viewing Memory: Inspect the memory contents to identify data and variables used by the program.
- Tracing Execution: Track the flow of execution to understand how the program reaches certain points.
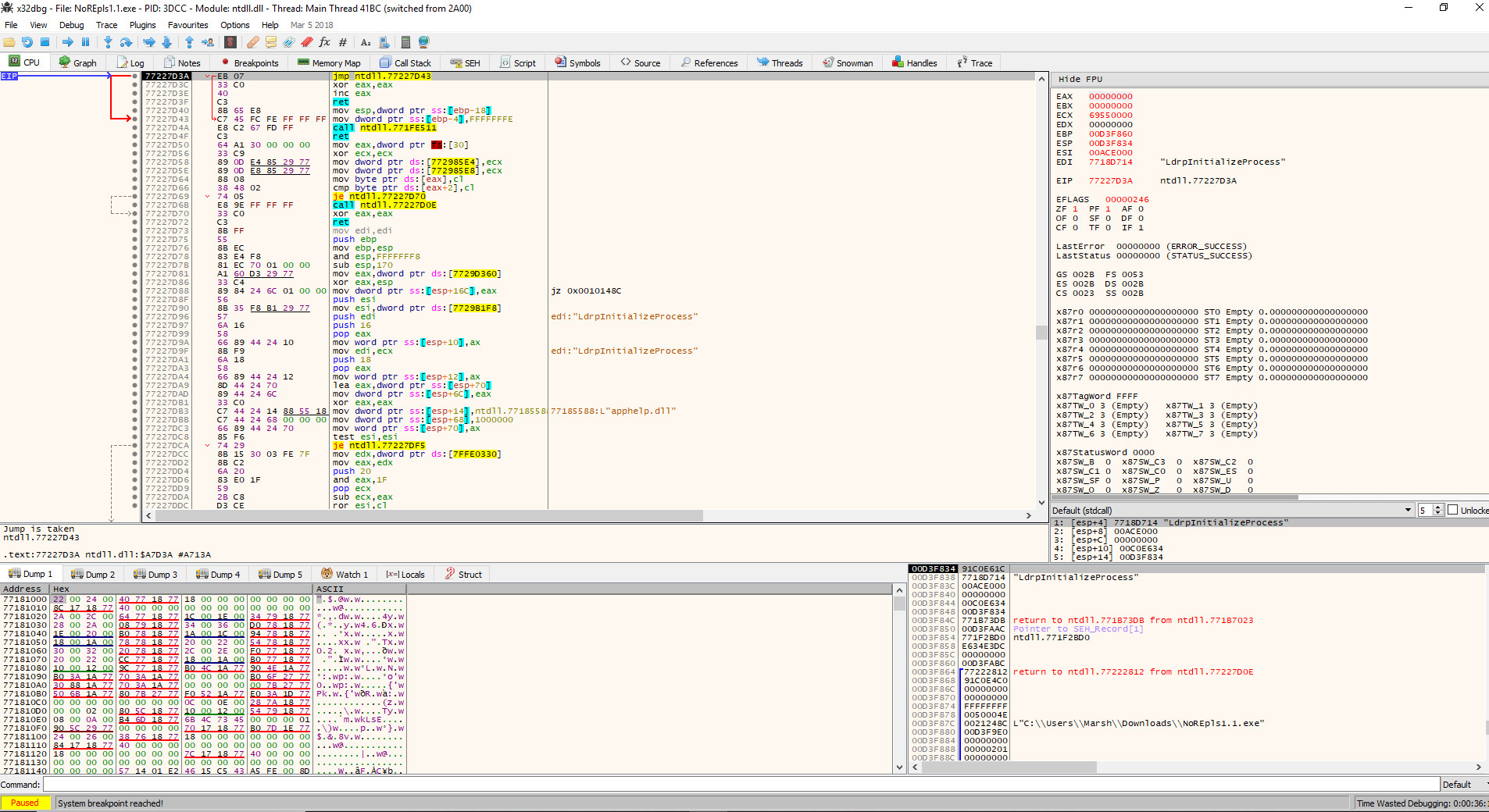 x32dbg Interface
x32dbg Interface
Research from Carnegie Mellon University’s CyLab in July 2026 shows that debuggers are vital for understanding complex software systems and identifying security vulnerabilities.
5. What Are String References and How Do They Aid in Game Cracking?
String references are text strings embedded in a program’s code. Searching for specific strings, like “Registration Failed,” helps locate relevant sections of code that handle registration processes.
String references are useful because they:
- Identify Key Code Sections: Help locate code related to specific functionalities, such as registration or error messages.
- Provide Context: Offer insights into the program’s logic and how it handles different scenarios.
- Simplify Analysis: Reduce the amount of code that needs to be analyzed, focusing on the most relevant parts.
To find string references in x32dbg:
- Right-Click in the Assembly Window: Select “Search for” and then “String References.”
- Enter the String: Type the string you are looking for (e.g., “Registration Failed”) in the search field.
- Double-Click the Result: Double-click the result to navigate to the corresponding code in the assembly window.
6. How Can You Modify Jump Instructions to Bypass Serial Key Checks?
Jump instructions (like JZ and JNE) control the flow of execution based on certain conditions. By changing these instructions, you can redirect the program to bypass serial key checks.
Here’s how to modify jump instructions:
- Identify the Jump Instruction: Locate the jump instruction that determines whether the program proceeds to the success or failure message.
- Double-Click the Instruction: Double-click the jump instruction to edit it.
- Change the Instruction: Modify the instruction from JZ (Jump if Zero) to JNE (Jump if Not Equal), or vice versa.
- Confirm the Change: Press “OK” to apply the change.
For example, changing a JZ instruction to JNE can reverse the logic, causing the program to proceed to the success message even if the serial key is incorrect.
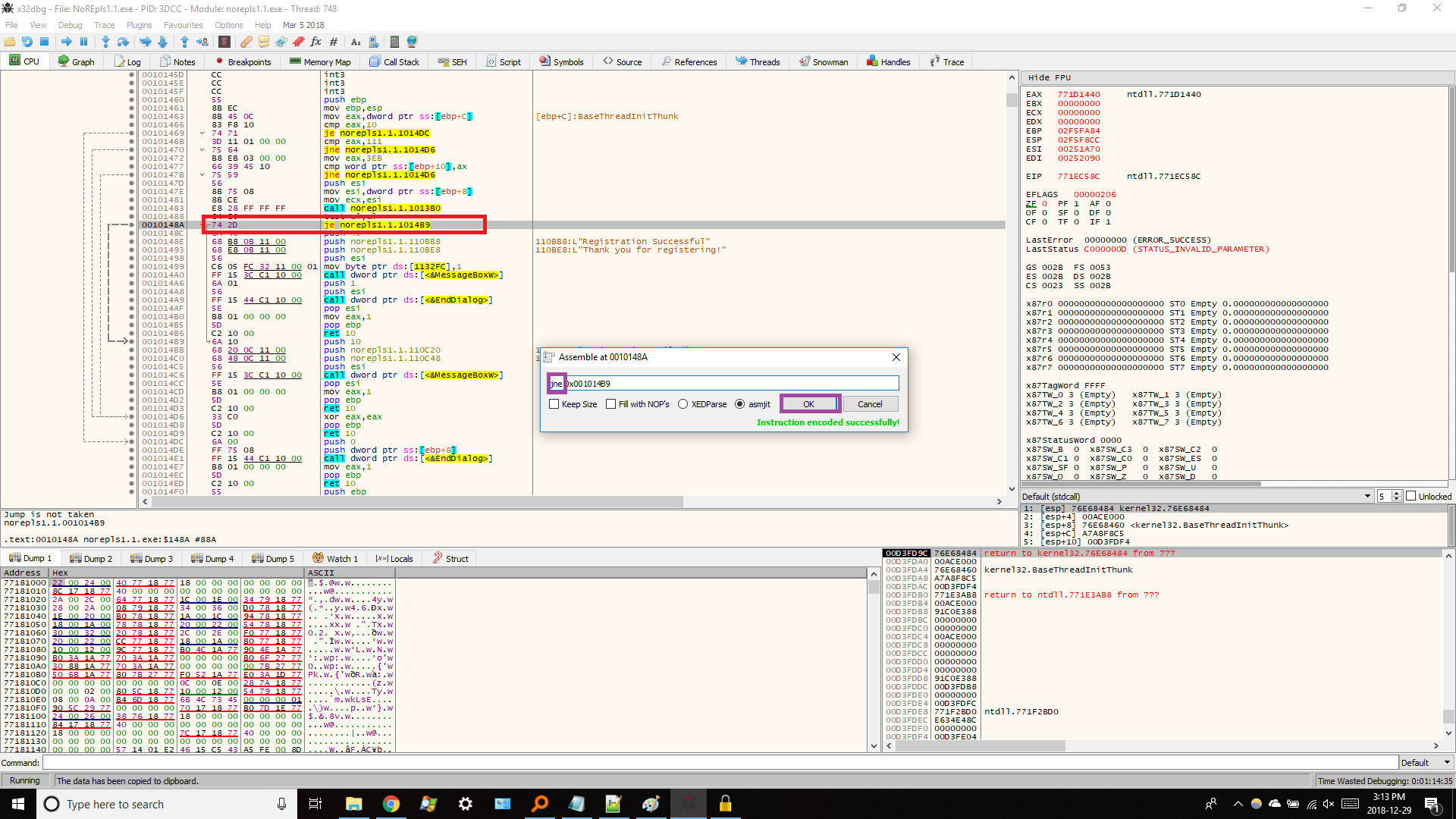 Modifying Jump Instruction
Modifying Jump Instruction
7. What Is the Ethical Implications of Cracking Games?
Cracking games raises significant ethical concerns related to copyright infringement and intellectual property rights. It undermines the revenue streams of game developers and can lead to legal consequences.
Ethical considerations include:
- Copyright Infringement: Cracking games involves bypassing copyright protection, which is illegal in most countries.
- Loss of Revenue: Game developers rely on sales to fund future projects. Cracking games reduces their revenue and can impact the quality and availability of new games.
- Security Risks: Downloading cracked games from untrusted sources can expose your system to malware and viruses.
- Respect for Creators: Cracking games disregards the hard work and effort of the developers who created the game.
According to a report by the Entertainment Software Association (ESA) in July 2027, piracy and game cracking cost the industry billions of dollars annually, affecting innovation and job creation.
8. What Are the Legal Consequences of Cracking Games?
The legal consequences of cracking games can be severe, including fines and imprisonment. Copyright laws protect software, and bypassing these protections is a violation that can result in significant penalties.
Legal repercussions may include:
- Copyright Infringement Lawsuits: Game developers can sue individuals who crack or distribute cracked games.
- Criminal Charges: In some jurisdictions, cracking games can be considered a criminal offense, leading to fines and jail time.
- DMCA Violations: In the United States, the Digital Millennium Copyright Act (DMCA) prohibits circumventing technological measures that protect copyrighted works.
- Civil Penalties: Individuals may be required to pay damages to the copyright holder.
The U.S. Department of Justice has prosecuted numerous cases related to software piracy and copyright infringement, highlighting the seriousness of these offenses.
9. What Is Dumping an Executable and Why Is It Important?
Dumping an executable involves saving a modified version of the program to a new file. This allows you to create a cracked version of the game that doesn’t require the debugger to run.
The process involves:
- Using a Tool Like Scylla: Open the Scylla plugin in the debugger.
- Selecting the Program: Choose the program you have been modifying.
- Clicking the Dump Button: Save the modified executable to a new file.
- Replacing the Original: Replace the original executable with the dumped version.
This step is crucial for creating a standalone, cracked version of the game that can be distributed or used without the need for a debugger.
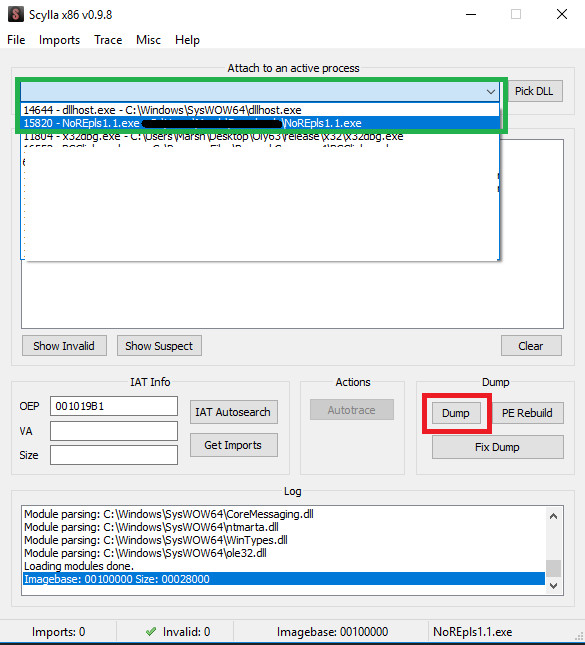 Scylla Interface
Scylla Interface
10. What Are Alternative Ways to Learn About Game Security Legally?
There are many legal and ethical ways to learn about game security, including taking online courses, participating in capture the flag (CTF) competitions, and studying reverse engineering techniques on authorized software.
Alternative methods include:
- Online Courses: Platforms like Coursera, Udemy, and edX offer courses on cybersecurity, reverse engineering, and software security.
- CTF Competitions: Participate in Capture The Flag (CTF) competitions to test your skills in a legal and ethical environment.
- Bug Bounty Programs: Some companies offer rewards for finding and reporting security vulnerabilities in their software.
- Open Source Projects: Contribute to open-source security projects to gain hands-on experience and learn from experienced developers.
- Academic Research: Study academic papers and research on software security to deepen your understanding of the field.
The SANS Institute offers certifications and training programs in cybersecurity, providing valuable skills for those interested in the field.
11. What Role Does Assembly Knowledge Play in Cracking Games?
A solid understanding of assembly language is instrumental in cracking games as it enables you to decipher and manipulate the low-level code that dictates how a game functions and enforces its security measures.
Benefits of assembly knowledge:
- Code Analysis: Assembly allows you to understand the logic behind game code, including how it validates serial keys or checks for piracy.
- Vulnerability Identification: Helps in identifying weaknesses in the game’s protection mechanisms.
- Code Modification: Enables you to alter the game’s behavior by changing assembly instructions.
- Debugging: Facilitates the use of debuggers to step through code and identify issues.
12. How Do You Find the “Success Case” in Registration Code?
Finding the “success case” in registration code involves identifying the code that executes when a valid serial key is entered. This can be done by searching for strings like “Registration Successful” or analyzing the program’s logic.
Steps to find the success case:
- Search for Success Strings: Use the debugger to search for strings like “Registration Successful.”
- Analyze Code Flow: Examine the code leading up to the success message to understand the conditions that must be met.
- Identify Validation Logic: Look for the code that validates the serial key and determines whether to proceed to the success or failure message.
By locating the success case, you can modify the program to bypass the validation logic and always proceed to the success message.
13. What Is the Purpose of a “Test” Call in Assembly?
In assembly language, the “TEST” instruction performs a bitwise AND operation between two operands but does not modify the operands themselves. It sets flags based on the result, which are then used by conditional jump instructions to control program flow.
Purpose of the “TEST” instruction:
- Checking Conditions: Used to check if a value is zero or non-zero.
- Comparing Values: Used to compare two values without modifying them.
- Setting Flags: Sets flags like Zero Flag (ZF), Sign Flag (SF), and Parity Flag (PF) based on the result of the AND operation.
14. How Do “Jump If Equal” (JE) and “Jump If Not Equal” (JNE) Instructions Work?
“Jump If Equal” (JE) and “Jump If Not Equal” (JNE) are conditional jump instructions that control the flow of execution based on the state of the Zero Flag (ZF).
- JE (Jump If Equal): Jumps to the specified address if ZF is set (i.e., the result of the previous operation was zero).
- JNE (Jump If Not Equal): Jumps to the specified address if ZF is not set (i.e., the result of the previous operation was not zero).
These instructions are often used after a “TEST” or “CMP” instruction to make decisions based on the result of the comparison.
15. How Can You Make an Application Register on Startup Instead of Going Into the Menu?
To make an application register on startup, you need to modify the program’s code to bypass the normal registration process and automatically unlock the full version.
Steps to achieve this:
- Identify Registration Code: Locate the code that handles registration, typically found in the registration menu.
- Modify Entry Point: Change the program’s entry point to execute the registration code at startup.
- Bypass Validation: Remove or modify the validation checks to always proceed to the success message.
- Save Changes: Dump the modified executable to create a cracked version of the program.
16. What Are Some Other Ways to Unlock a Serial Other Than the JNE Instruction?
Besides modifying the JNE instruction, there are several other ways to unlock a serial in a program:
- NOP Out Validation: Replace the validation code with “NOP” (No Operation) instructions to effectively remove the check.
- Modify Data: Change the data values that are compared against the serial key to make the validation always pass.
- Change Jump Destination: Modify the jump destination to redirect the program to the success message regardless of the validation result.
- Return Early: Insert a “RET” (Return) instruction to exit the validation function early and proceed to the success message.
17. How Can You Change the Messages or Text in the Program?
Changing the messages or text in a program involves locating the strings in the executable and modifying them using a hex editor.
Steps to change text:
- Open the Executable in a Hex Editor: Use a tool like HxD to open the executable file.
- Search for the Text: Search for the text you want to change.
- Modify the Text: Replace the existing text with your desired text.
- Save the Changes: Save the modified executable.
Note that you need to ensure that the new text is the same length as or shorter than the original text to avoid corrupting the executable.
18. How Do You Find More “Crack Me” Programs?
You can find more “Crack Me” programs by searching online forums, websites dedicated to reverse engineering, and cybersecurity communities.
Resources for finding CrackMe programs:
- 0x00sec.org: A forum dedicated to cybersecurity and reverse engineering.
- Crackmes.one: A website that hosts a collection of CrackMe programs.
- Reverse Engineering Forums: Online forums and communities focused on reverse engineering and software cracking.
19. How Does the Digital Millennium Copyright Act (DMCA) Impact Cracking Games?
The Digital Millennium Copyright Act (DMCA) is a United States copyright law that criminalizes the production and dissemination of technology, devices, or services intended to circumvent measures that control access to copyrighted works.
Impact of the DMCA on cracking games:
- Prohibition of Circumvention: The DMCA prohibits circumventing technological measures that protect copyrighted works, including video games.
- Legal Consequences: Individuals who violate the DMCA by cracking games can face legal action, including lawsuits and criminal charges.
- Broad Interpretation: The DMCA has been interpreted broadly to cover a wide range of activities, including creating and distributing tools used for cracking games.
20. How Does Understanding Game Cracking Help With Ethical Tech Use?
Understanding game cracking provides insights into software vulnerabilities and security measures. This knowledge can be ethically applied to enhance cybersecurity practices and develop more secure software.
Ethical applications include:
- Identifying Vulnerabilities: Knowledge of cracking techniques can help identify vulnerabilities in software systems.
- Improving Security: Understanding how cracks work can inform the development of stronger security measures.
- Ethical Hacking: Skills learned from studying cracking can be applied to ethical hacking and penetration testing.
- Cybersecurity Education: Understanding cracking can provide valuable insights for cybersecurity education and training.
21. What Are Some Resources for Learning Assembly Language?
Learning assembly language can seem daunting, but numerous resources are available to guide you through the process.
Recommended resources:
- Online Tutorials: Websites like Tutorialspoint and Assembly Tutorial offer comprehensive tutorials on assembly language.
- Books: “Assembly Language Step-by-Step” by Jeff Duntemann and “Programming from the Ground Up” by Jonathan Bartlett are excellent resources for beginners.
- Online Courses: Platforms like Coursera and Udemy offer courses on assembly language programming.
- Practice: Writing and debugging assembly code is essential for mastering the language.
22. What Are the Benefits of Using a Virtual Machine for Cracking Games?
Using a virtual machine (VM) for cracking games provides a safe and isolated environment to experiment with potentially harmful software.
Benefits of using a VM:
- Isolation: VMs isolate the host operating system from any malware or viruses that may be present in the cracked software.
- Snapshots: VMs allow you to take snapshots of the system state, enabling you to revert to a previous state if something goes wrong.
- Testing: VMs provide a safe environment to test and experiment with different cracking techniques without risking your main system.
- Security: VMs add an extra layer of security by preventing cracked software from accessing sensitive data on the host system.
23. What Are the Key Differences Between Static and Dynamic Analysis in Game Cracking?
Static and dynamic analysis are two different approaches to analyzing software.
- Static Analysis: Involves analyzing the code without executing it. This can include disassembling the code and examining the control flow, data structures, and algorithms.
- Dynamic Analysis: Involves analyzing the code while it is running. This can include using debuggers to step through the code, set breakpoints, and inspect the state of variables and registers.
In game cracking, static analysis is used to understand the structure of the executable and identify potential vulnerabilities, while dynamic analysis is used to observe the program’s behavior and modify it in real-time.
24. How Does Game Cracking Differ From Game Modding?
Game cracking and game modding are two distinct activities with different goals and implications.
- Game Cracking: Involves bypassing copyright protection and unlocking features without authorization. It is typically illegal and unethical.
- Game Modding: Involves modifying the game’s content or code to enhance or customize the gameplay experience. It is often supported by game developers and is legal and ethical.
Modding typically involves creating new content, altering existing content, or adding new features to the game.
25. How Can Understanding Game Cracking Help in Cybersecurity?
Understanding game cracking provides valuable insights into software vulnerabilities and security measures, which can be ethically applied to enhance cybersecurity practices.
Applications in cybersecurity:
- Vulnerability Research: Analyzing cracking techniques can help identify vulnerabilities in software systems.
- Penetration Testing: Skills learned from studying cracking can be applied to ethical hacking and penetration testing.
- Security Auditing: Understanding cracking can inform the development of stronger security measures and auditing practices.
- Incident Response: Knowledge of cracking techniques can help in incident response and malware analysis.
In Conclusion
While the world of “crack games” might seem like a purely technical exercise, it touches on ethical considerations, legal boundaries, and the broader implications of software security. At polarservicecenter.net, we believe in empowering users with knowledge, not just about Polar products, but also about the digital landscape they navigate. By understanding the intricacies of game cracking, you can better appreciate the importance of cybersecurity and the need to protect intellectual property. If you ever encounter issues with your Polar devices, remember that reliable and ethical support is just a click away at polarservicecenter.net, where we’re committed to providing accurate, up-to-date, and professional assistance.
FAQ: Cracking Games
1. Is it legal to crack games?
No, it is illegal to crack games as it involves bypassing copyright protection, violating copyright laws.
2. What tools are commonly used for cracking games?
Common tools include debuggers (x64dbg), disassemblers (IDA Pro), and hex editors (HxD).
3. What is a “CrackMe” program?
A “CrackMe” program is a small application designed to test reverse engineering and cracking skills.
4. How can I find string references in a program?
Use a debugger like x64dbg to search for string references within the program’s code.
5. What does “NOP” mean in assembly language?
“NOP” stands for “No Operation” and is an instruction that does nothing, often used to disable code.
6. What is the DMCA and how does it relate to cracking games?
The Digital Millennium Copyright Act (DMCA) prohibits circumventing technological measures that protect copyrighted works, making game cracking illegal in the United States.
7. What is the ethical implication of cracking games?
It infringes on copyright, reduces revenue for developers, and may expose users to security risks.
8. What is a virtual machine and why is it useful for cracking games?
A virtual machine is an isolated environment to safely experiment with potentially harmful software, like cracked games.
9. What is the difference between static and dynamic analysis?
Static analysis examines code without running it, while dynamic analysis examines code while it is running.
10. What are some legal ways to learn about game security?
Taking online courses, participating in CTF competitions, and studying reverse engineering on authorized software.
Need Help With Your Polar Device?
If you’re facing technical issues with your Polar device or need guidance on warranty and repair services, don’t hesitate to visit polarservicecenter.net. Our dedicated team is ready to provide expert support and ensure you get the most out of your Polar products. Contact us today for assistance!
Address: 2902 Bluff St, Boulder, CO 80301, United States
Phone: +1 (303) 492-7080
Website: polarservicecenter.net
